https://ift.tt/2jI0yLW
Much like humans, computers can contract nasty viruses that completely wreak havoc on their systems. It’s believed that there are over 100,000 computer viruses, though some experts contend that there are over a million. The good news is that many of the viruses are not in circulation and are merely a part of collections. However, there are some that have been released, and in some cases, they caused massive devastation. These are 10 of the most notorious.
10. The Morris Worm
Robert Morris, Jr. is the son of a famous American cryptographer and pioneering computer scientist, Robert Morris, Sr. In 1988, he was a graduate student in Computer Science at Cornell, when he wrote an experimental program called a worm. The worm was 99 lines of code and it had the ability to self-replicate and self-propagate.
On November 2, 1988, Morris loaded his program onto the internet using a computer at MIT. However, Morris made a mistake in his coding and the worm spread quickly. Since the internet wasn’t as widespread then as it is now, the Morris Worm managed to infect 10 percent of all computers on the internet (which was about 6,000).
The program ran a bunch of invisible tasks and this caused computers around the United States to crash or become catatonic. When Morris realized what was happening, he contacted a friend at Harvard and they came up with a solution. They tried to send out an anonymous message on how to fix it, but it was too late and the message got lost in the traffic caused by the worm.
Computer programmers around the country worked for days to figure out how to debug the computers. In total, it cost anywhere from $200 to more than $53,000 to fix an infected computer. After investigating, all evidence in the coding of the worm pointed to Morris. He was convicted of violating the Fraud and Abuse Act and handed a sentence of three years of probation, 400 hours of community service, and fined $10,050.
9. The Omega Time Bomb
Omega Engineering is a Stamford, Connecticut based company that designs and manufactures high tech instrumentation. On the morning of July 31, 1996, an employee in the Computer Numeric Control department started up the file server that controlled all the manufacturing machines. However, the server didn’t boot up and instead a message popped up that said that the file server was being fixed.
However, quite the opposite happened. Instead of fixing the files, it deleted them. Even worse, the virus destroyed any way of finding the programs again. Computer Security Journal said that the lines of code were scattered like a handful of sand thrown onto a beach. Omega was sure they had backups on tape and on local computers, but when they went to retrieve them, they could not be found.
When the employees realized what had happened, the first person they called was Tim Lloyd, a former employee who oversaw the computer network. He had been with the company for 10 years, but lost his job three weeks before the server crash because of problems with his attitude. Over the course of a year, Lloyd’s personality had changed and he became an angry man who lashed out at co-workers. His attitude also led to him purposely bottlenecking projects, which slowed production. He was given several warnings before he was fired on June 10, 1996.
When Omega realized how much information they had lost, they called the police who, in turn, called in the Secret Service. When they investigated, they found that the virus was just six lines of code that worked like a time bomb. When someone logged on July 31, 1996, it would delete all of Omega’s computer files. The most obvious suspect was Lloyd and the Secret Service looked at his home computer and found the same six lines of code. They determined that Lloyd was planning on quitting and he made the time bomb virus at home. He then installed it at work after everyone had left for the night. However, before he got a chance to quit, he was fired.
Lloyd was arrested and sentenced to three and a half years in prison, and ordered to pay $2 million in restitution. At the time, it was the worst act of work-related computer sabotage. It cost Omega over $10 million in lost business and $2 million in reprogramming cost. They also had to lay off 80 people. It took years for Omega to overcome the virus attack, but they are still in business today.
8. Melissa
The Melissa virus started to spread on March 26, 1999, via email. The subject line of the email was “Important message from [Sender’s Name]” and the body of the email was, “Here is that document you asked for…don’t show anyone else ;-).” Finally, there was a Microsoft Word document labeled “list.doc.” When people would open the document, it would send out the same “Important Message” email to the first 50 addresses in the person’s Outlook address book.
The virus spread to hundreds of thousands of computers in the first several days. In some cases, it caused servers to shut down. Even Microsoft and Intel were infected. Microsoft chose to shut down their outgoing internet email service to stop the spread. In total, it’s estimated that the Melissa virus caused around $400 million in damage.
The virus was traced back to David L. Smith, a network programmer who lived in Trenton, New Jersey. Smith had hacked an America Online account and launched the virus from his apartment. He was arrested less than a week after the virus was released. He said that he named the virus Melissa after a topless dancer in Florida. He was sentenced to 20 months in federal prison.
When he was asked why he did it, Smith basically said that he did it to see if he could do it. Fair enough, we guess.
7. LoveBug aka ILOVEYOU
On May 4, 2000, people in the Philippines started getting emails with the subject line “ILOVEYOU.” The body of the email read, “Kindly check the attached LOVELETTER coming from me.” Finally, there was an attachment with a file name like “LOVE-LETTER-FOR-YOU.TXT.” Many people who got the email couldn’t resist the thought of someone sending them a love letter out of the blue, so millions tried to open what they thought was a text file. And as you probably have guessed, it was, of course, a virus.
By today’s standards, the virus was pretty tame. It would make duplicate copies of media files and documents. It would also email the virus’ creator the user names and passwords of infected computers, which would allow him to log onto the internet for free. However, the real problem was that it could email a copy of itself to every email address in the infected computers’ Microsoft Outlook address book. At the time, not many people saw the importance of having things like an up-to-date antivirus program. As a result, according to the BBC, the LoveBug (as it was sometimes called) spread to 45 million computers in the first couple of days.
When programmers looked at the code, they found an email address embedded in it and the worm was traced back to 24-year-old Onel de Guzman, who was a student at the AMA Computer College in the Philippines. De Guzman had recently dropped out because his undergraduate thesis, which was to commercialize a Trojan horse that stole passwords, was rejected.
After the virus was released, De Guzman went into hiding. When he reemerged several days later, he was arrested along with one of his friends, Reomel Ramones. However, there were no laws regarding malware in the Philippines so neither man was ever charged or prosecuted. De Guzman says that the virus was “probably” his creation and admitted that he may have “accidentally” let it out of captivity.
The LoveBug became the first virus to successfully spread using social engineering, but it certainly wouldn’t be the last.
6. Agent.btz
In the fall of 2008, the U.S. Military’s computer network was hit by a variation of a SillyFDC worm. At the time, the SillyFDC worm was a fairly benign worm; before the attack, a SillyFDC worm was listed as “Risk Level 1: Very Low.” One reason the worm wasn’t super effective is that it wasn’t transferred through something like email. Instead, it was transferred via storage devices, like thumb drives.
However, a new variation of the worm, called Agent.btz, infected a military laptop at a base in the Middle East when someone inserted an infected flash drive. The laptop was connected to the U.S. Central Command and the virus was uploaded to the network. From there, the virus spread undetected through both classified and unclassified systems. Once the virus was in place, data could be secretly transferred to different foreign servers.
In a process called “Operation Buckshot Yankee,” it took the military 14 months to finally clear out the virus and it led to the formation of a new unit called the United States Cyber Command.
The leading theory is that the virus was an espionage attack by a foreign country, most likely Russia.
5. Flashback
Apple has long promoted that Macs are much safer than PCs because, Apple says, they are less likely to get viruses or malware. There are two big reasons for this. The first is that Microsoft Windows is used by a vast majority of computers. Even in 2016, Macs only account for 7.4 percent of home computer sales. This makes Windows a much bigger target. Secondly, it is much harder to make changes to Mac’s operating system, macOS (formerly OS X). There are areas of macOS that are walled off and you need administrative privilege to change it, meaning its operating system has a limited amount of points of intrusion.
However, that doesn’t mean Macs are invincible from viruses. The most notorious of them was discovered in September 2011. How it worked was that it was disguised as an Adobe Flash installer and it got around Mac’s security because there was an unpatched vulnerability in Java. The result was that 650,000 Macs, which was about 1.5 percent of all Macs at the time, were infected.
The Trojan horse virus did two things. The first is that it created a backdoor in the system so data, like passwords, could be stolen. It also took control of the computers, making them a botnet, which is when one central computer controls a collection of zombie computers.
By February 2012, Mac released a security tool to remove the virus and Oracle, who makes Java, fixed the vulnerability.
4. Sasser and Netsky-AC
The Sasser virus was first detected on April 30, 2004. It was different from other viruses at the time because with other viruses, users needed to do a task to infect their computer, like open a file. Instead, the Sasser virus passed through the Local Security Authority Subsystem Service (LSASS). It would scan random computers until it found a vulnerable system and then it would copy itself as an executable file to the computer. When the computer was booted, the virus would install itself.
Microsoft knew about the vulnerability and issued a patch for it on April 13, 17 days before the virus was first detected. However, not every computer had updated the patch and this left them exposed. In the two days after the virus was detected, a cleanup tool was downloaded 1.5 million times.
One thing that really set Sasser apart from other viruses is that in the days after the virus was released, an email started circulating with a file that was supposed to fix it. Instead, it was another virus called Netsky-AC.
The viruses didn’t cause any permanent damage. However, it did cause computers to crash and reboot more often. In total, hundreds of thousands of computers were infected.
After the viruses were released, Microsoft offered a $250,000 reward for information on the author or authors. Two people turned in 18-year-old computer student Sven Jaschan, who was responsible for writing both Sasser and Netsky-AC. He was arrested and faced up to five years in jail; instead, he got a 21-month suspended sentence.
3. SQL Slammer
The fastest spreading computer worm in history, the SQL Slammer virus is also known as w2.SQLSlammer.worm, Sapphire, w32.SQLexp.worm, and Helkern. The worm started to spread at 12:30 EST on January 25, 2003. The virus would scan the entire internet for random IP addresses looking for vulnerable Microsoft SQL 2000 servers. The number of computers infected doubled every 8.5 seconds and within 10 minutes, 75,000 hosts, which was about 90 percent of vulnerable hosts, were infected.
The virus didn’t really effect home computers. Instead, it caused network outages, slowed down internet service, and denied some hosts access to the internet. This effected airline flights, interfered with electronics, and caused ATM failures. It is estimated that the virus cost $1 billion in lost revenue.
A major investigation was launched, but the author has never been identified.
2. Storm Worm
On January 19, 2007, computers in the United States and Europe started getting emails with the subject line “230 dead as storm batters Europe,” and then there was an attachment called video.exe. Of course, the attachment wasn’t a video; it was a Trojan horse virus. After infecting the computer, it created a backdoor which the author could use later to get data, and it added the computer to the botnet. The botnet was then used to post spam.
One of the reasons that the virus was initially successful was because, at the time when it was sent, bad storms were raging in Europe. Later, the subject was changed to over two dozen different headlines including “A killer at 11, he’s free at 21 and…”, “Chinese missile shot down USA aircraft”, and “President of Russia Putin dead”, just to name a few.
According to IBM, by February 2008 the worm had taken control of enough computers to perform spam attacks that were making the creators $2 million per day. As for who the creators were, it’s believed that the virus originated in Russia, but beyond that not much is known.
1. Code Red
The first version of the Code Red worm was discovered on July 12, 2001, by several employees at eEye Digital Security. They spent all night analyzing the worm and while working on it, they drank Mountain Dew Code Red. So, they called the virus Code Red, and the name stuck.
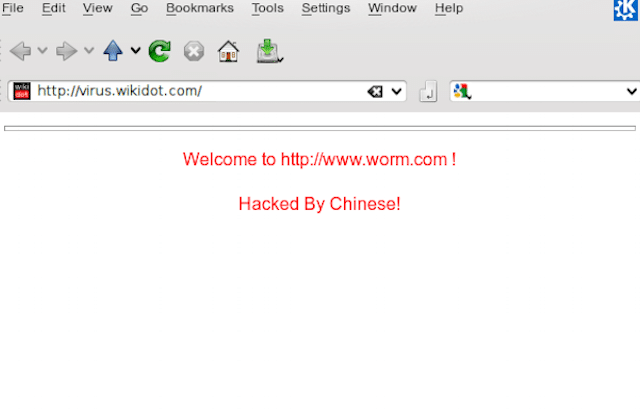
The first variation of Code Red didn’t spread fast and didn’t do much damage. Some websites were defaced and they said “Welcome to China http://www.worm.com ! Hacked by Chinese!” However, on the 20th of July, the virus stopped trying to infect other servers and a launched denial-of-service attack on the White House’s web page. Fortunately, the White House was able to stop the attack by changing IP addresses.
Code Red version 2, on the other hand, was much more problematic. At the time, it was the fastest moving computer virus. It was discovered at 5:00 p.m. EST on July 19, 2001, and within 14 hours, over 359,000 computers were infected. In total, it’s believed that the worm infected 1 million of 5.9 million web servers. This caused internet traffic to slow but didn’t do any damage to the servers themselves.
Code Red version 2 was also one of the most costly viruses. In July and August, the virus led to $2.6 billion in damages. The virus is believed to have originated at a university in China. However, it has never been confirmed.
Robert Grimminck is a Canadian freelance writer. You can friend him on Facebook, follow him on Twitter, follow him on Pinterest or visit his website, or his true crime YouTube channel.
TECH
TRENDS,AMAZING
via Toptenz.net http://www.toptenz.net
May 13, 2018 at 07:22PM
.png)
No comments:
Post a Comment